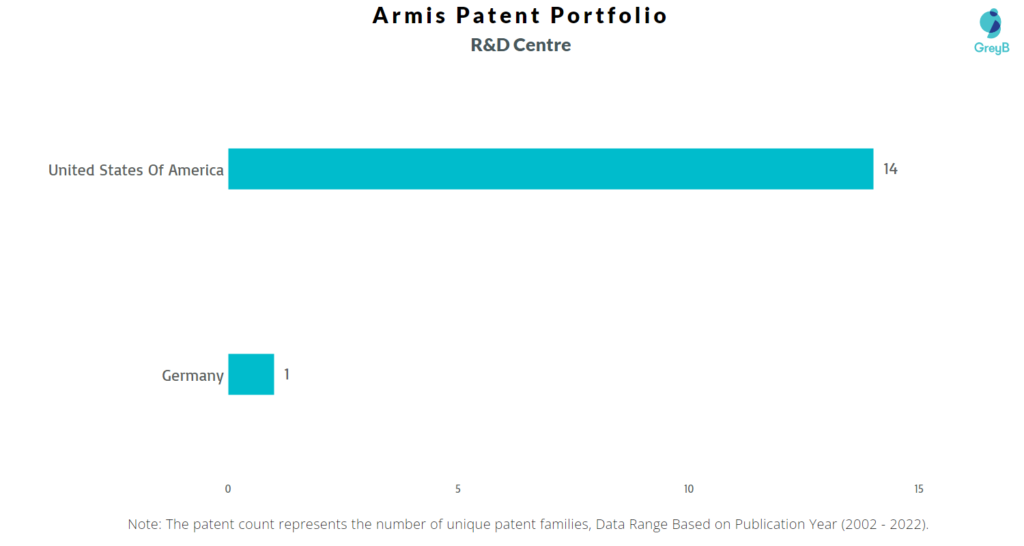
Armis Security has a total of 38 patents globally, out of which 8 have been granted. Of these 38 patents, more than 92% patents are active. The United States of America is where Armis Security has filed the maximum number of patents, followed by Canada and Europe. Parallelly, United States of America seems to be the main focused R&D center and also is the origin country of Armis Security.
Armis Security was founded in 2015. Armis Security develops an Internet of things (IoT) security solutions. The Company offers a platform to control and detect activity and threats on devices and networks, as well as provides protection to organizations from unmanaged and rogue devices including point of sale products, infusion pumps, security cameras and routers, production line sensors, printers, and televisions.
Do read about some of the most popular patents of Armis Security which have been covered by us in this article and also you can find Armis Security patents information, the worldwide patent filing activity and its patent filing trend over the years, and many other stats over Armis Security patent portfolio.
How many patents does the Founder and CEO of Armis Security have?
The Founder Nadir Izrael has 15, Tomer Schwartz has 23 patents and the CEO Yevgeny Dibrov have 0 patents.
How many patents does Armis Security have?
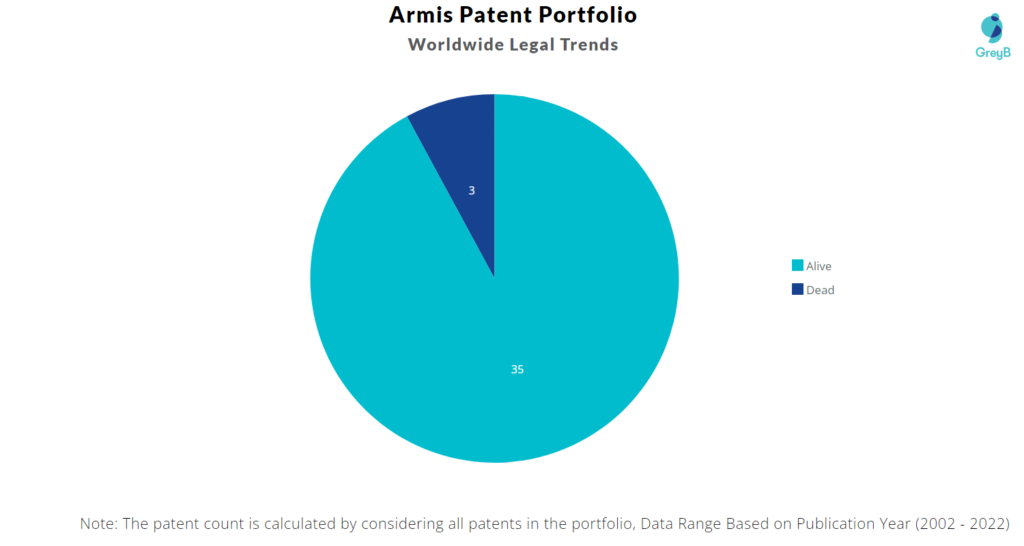
Armis Security has a total of 38 patents globally. These patents belong to 15 unique patent families. Out of 38 patents, 35 patents are active.
How Many Patents did Armis Security File Every Year?
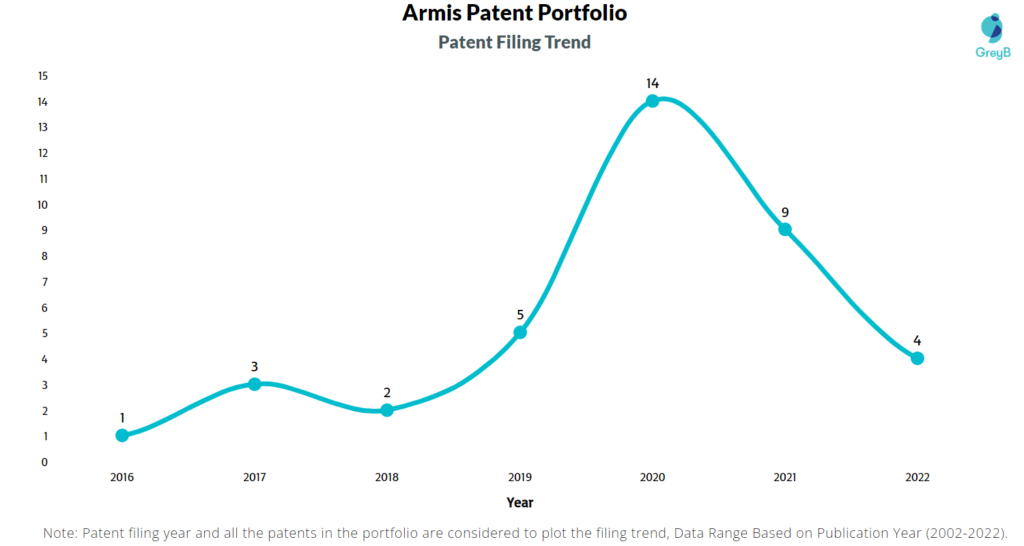
Are you wondering why there is a drop in patent filing for the last two years? It is because a patent application can take up to 18 months to get published. Certainly, it doesn’t suggest a decrease in the patent filing.
| Year of Patents Filing or Grant | Armis Applications Filed | Armis Patents Granted |
| 2016 | 1 | – |
| 2017 | 3 | – |
| 2018 | 2 | – |
| 2019 | 5 | 3 |
| 2020 | 14 | – |
| 2021 | 9 | 4 |
| 2022 | 4 | 1 |
How many Armis Security patents are Alive/Dead?
Worldwide Patents
How Many Patents did Armis Security File in Different Countries?
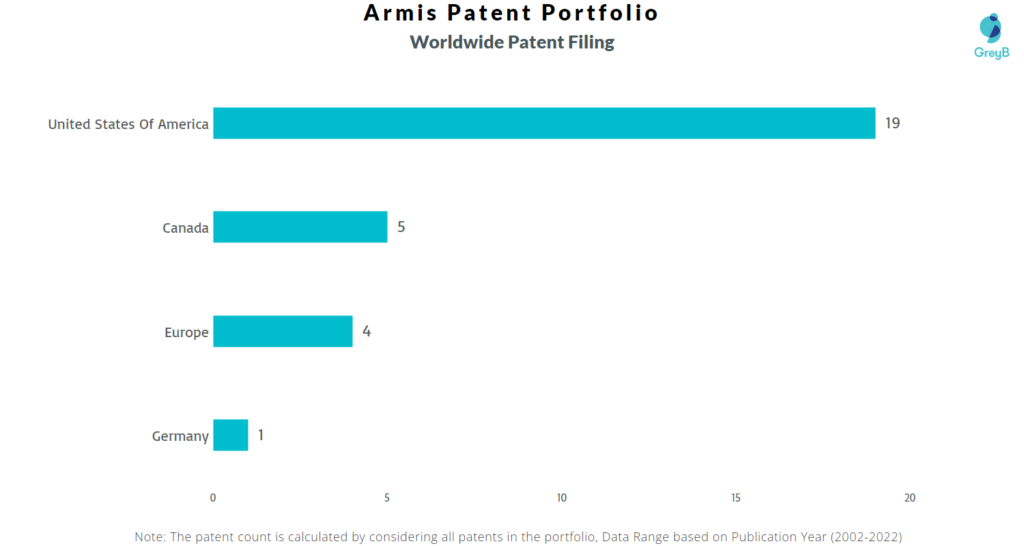
Countries in which Armis Security Filed Patents
| Country | Patents |
| United States Of America | 19 |
| Canada | 5 |
| Europe | 4 |
| Germany | 1 |
Where are Research Centers of Armis Security Patents Located?
What Percentage of Armis Security US Patent Applications were Granted?
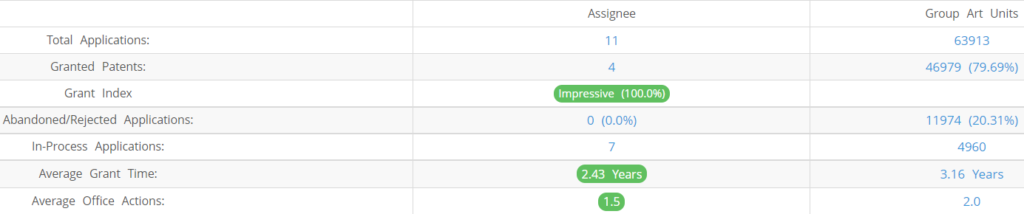
Armis Security (Excluding its subsidiaries) has filed 11 patent applications at USPTO so far (Excluding Design and PCT applications). Out of these 4 have been granted leading to a grant rate of 100.0%.
Below are the key stats of Armis Security patent prosecution at the USPTO.
Which Law Firms Filed Most US Patents for Armis Security?
| Law firm | Total Applications | Success Rate |
| M&B Ip Analysts Llc | 11 | 100.00% |
list of Armis Security Patents –
| Publication Number | Title |
| US20180124093A1 | Detection Of Vulnerable Wireless Networks |
| US10498758B1 | Network Sensor And Method Thereof For Wireless Network Vulnerability Detection |
| US10505967B1 | Sensor-Based Wireless Network Vulnerability Detection |
| US10511620B2 | Detection Of Vulnerable Devices In Wireless Networks |
| US20200106803A1 | Sensor-Based Wireless Network Vulnerability Detection |
| US20210185058A1 | Techniques For Resolving Contradictory Device Profiling Data |
| US20210203575A1 | System And Method For Determining Device Attributes Using A Classifier Hierarchy |
| US11102233B2 | Detection Of Vulnerable Devices In Wireless Networks |
| US11102082B1 | System And Method For Inferring Operating Systems Using Transmission Control Protocol Fingerprints |
| US20210264035A1 | Techniques For Detecting Exploitation Of Medical Device Vulnerabilities |
| US20210264036A1 | Techniques For Detecting Exploitation Of Manufacturing Device Vulnerabilities |
| US20210349774A1 | System And Method For Inferring Device Model Based On Media Access Control Address |
| US20220150264A1 | System And Method For Anomaly Detection Interpretation |
| US11363051B2 | System And Method For Mitigating Cyber Security Threats By Devices Using Risk Factors |
| US20220239682A1 | System And Method For Securing Networks Based On Categorical Feature Dissimilarities |
| US20220263853A1 | System And Method For Mitigating Cyber Security Threats By Devices Using Risk Factors |
| US20220278984A1 | System And Method For Operating System Distribution And Version Identification Using Communications Security Fingerprints |
| US20220311789A1 | System And Method For Detection Of Abnormal Device Traffic Behavior |
| US20220327221A1 | Techniques For Detecting Exploitation Of Medical Device Vulnerabilities |
| EP3422665B1 | Sensor-Based Wireless Network Vulnerability Detection |
| EP3948600A1 | System And Method For Mitigating Cyber Security Threats |
| EP4032250A1 | Techniques For Resolving Contradictory Device Profiling Data |
| EP4066465A1 | System And Method For Determining Device Attributes Using A Classifier Hierarchy |
| WO2020205258A1 | System And Method For Mitigating Cyber Security Threats |
| WO2021124027A1 | Techniques For Resolving Contradictory Device Profiling Data |
| WO2021137138A1 | System And Method For Determining Device Attributes Using A Classifier Hierarchy |
| WO2021171105A1 | Techniques For Detecting Exploitation Of Medical Device Vulnerabilities |
| WO2021171106A1 | Techniques For Detecting Exploitation Of Manufacturing Device Vulnerabilities |
| WO2021224744A1 | System And Method For Inferring Device Model Based On Media Access Control Address |
| WO2022101722A1 | System And Method For Anomaly Detection Interpretation |
| WO2022162530A1 | System And Method For Securing Networks Based On Categorical Feature Dissimilarities |
| WO2022208350A1 | System And Method For Detection Of Abnormal Device Traffic Behavior |
| CA3135483A1 | System And Method For Mitigating Cyber Security Threats |
| DE602018026350T2 | Sensor-Based Wireless Network Releases Detection |
| CA3158309A1 | Techniques For Resolving Contradictory Device Profiling Data |
| CA3165726A1 | System And Method For Determining Device Attributes Using A Classifier Hierarchy |
| CA3170192A1 | Techniques For Detecting Exploitation Of Manufacturing Device Vulnerabilities |
| CA3170191A1 | Techniques For Detecting Exploitation Of Medical Device Vulnerabilities |
