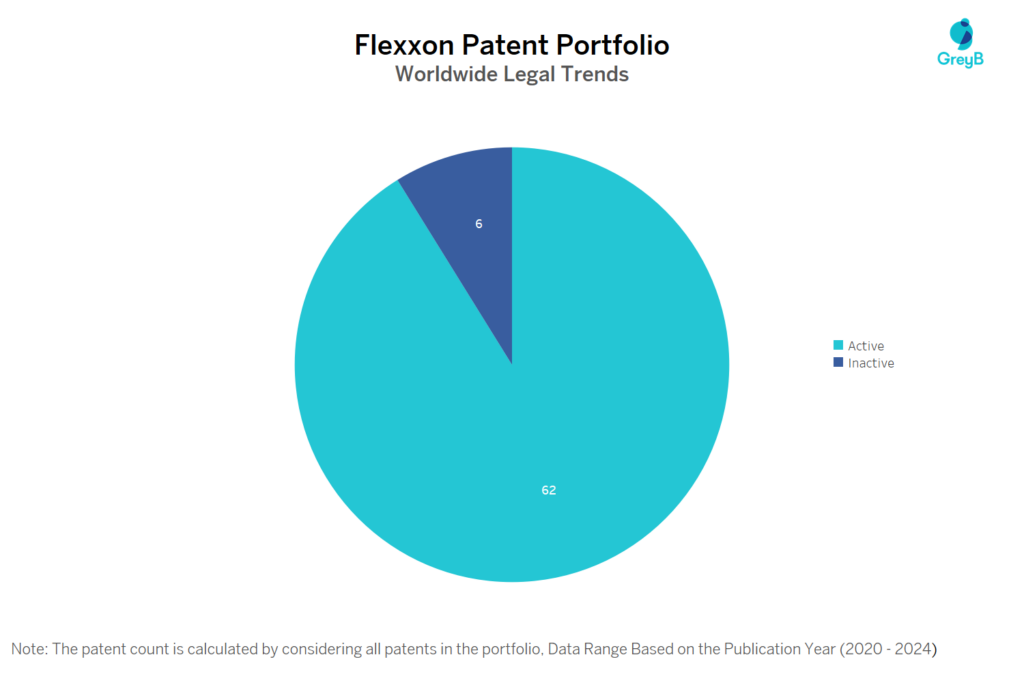
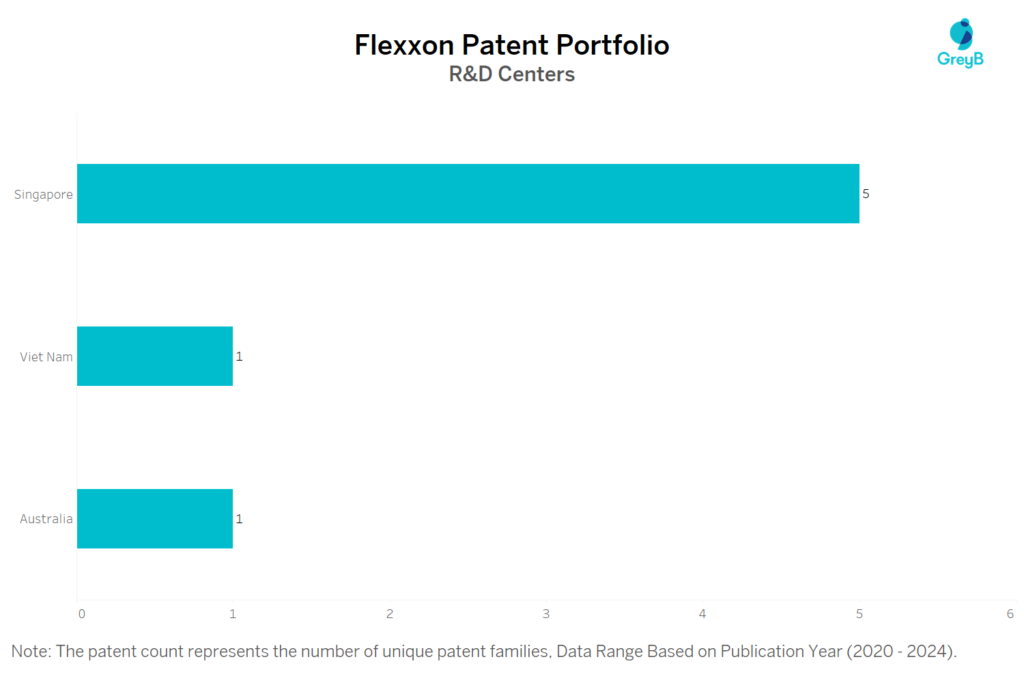
Flexxon has a total of 68 patents globally, out of which 39 have been granted. Of these 68 patents, more than 89% patents are active. Singapore is where Flexxon has filed the maximum number of patents, followed by United States of America and Australia. Parallelly, Singaporeseems to be the main focused R&D centre and also is the origin country of Flexxon.
Flexxon was founded in the year 2007. The company is specializing in hardware-based cybersecurity solutions and industrial NAND flash storage devices. It serves sectors like cybersecurity, industrial, medical, and automotive applications.
Do read about some of the most popular patents of Flexxon which have been covered by us in this article and also you can find Flexxon patents information, the worldwide patent filing activity and its patent filing trend over the years, and many other stats over Flexxon patent portfolio.
How many patents does Flexxon have?
Flexxon has a total of 68 patents globally. These patents belong to 7 unique patent families. Out of 68 patents, 62 patents are active.
How Many Patents did Flexxon File Every Year?
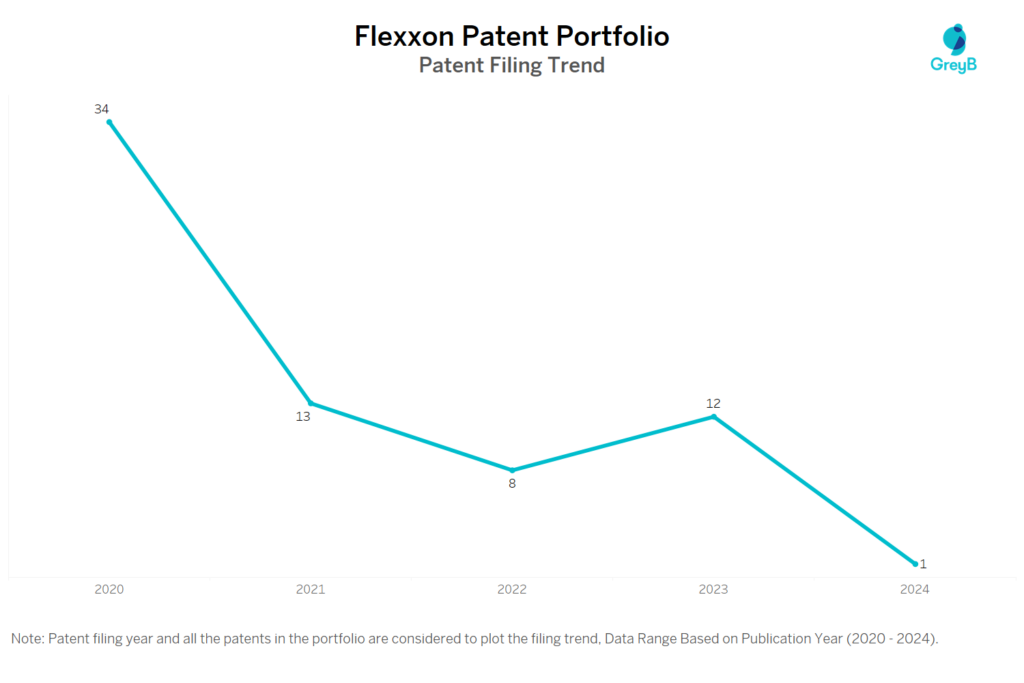
Are you wondering why there is a drop in patent filing for the last two years? It is because a patent application can take up to 18 months to get published. Certainly, it doesn’t suggest a decrease in the patent filing.
| Years | Application Year Count | Publication Year Count |
| 2024 | 1 | 12 |
| 2023 | 12 | 9 |
| 2022 | 8 | 9 |
| 2021 | 13 | 8 |
| 2020 | 34 | 1 |
How many Flexxon patents are Alive/Dead?
How Many Patents did Flexxon File in Different Countries?
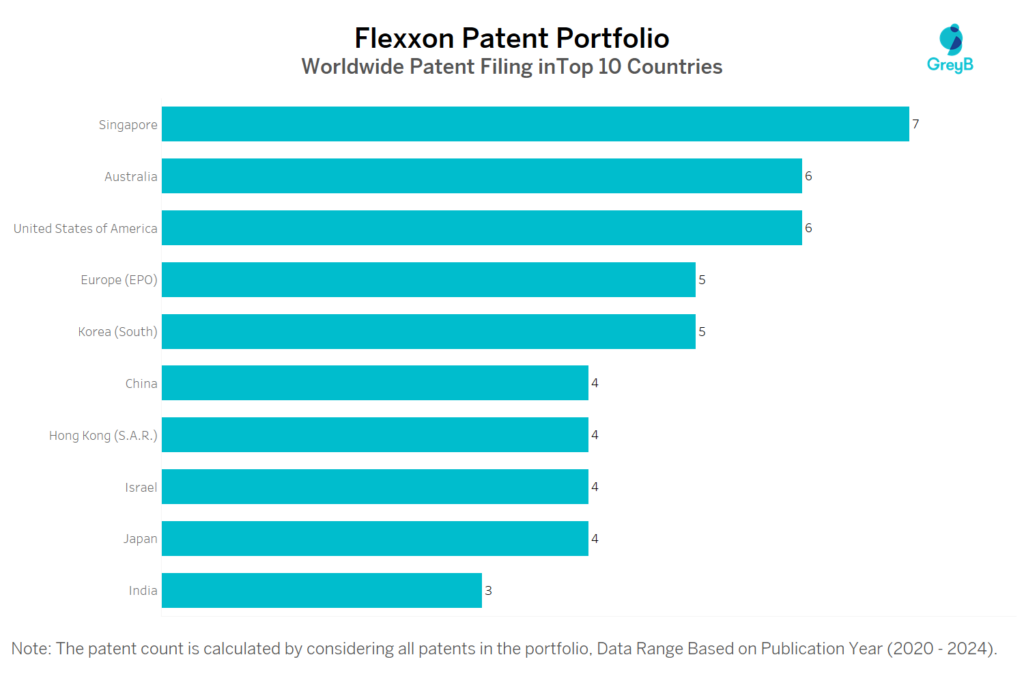
Countries in which Flexxon Filed Patents
| Country | Patents |
| Singapore | 7 |
| United States of America | 6 |
| Australia | 6 |
| Europe (EPO) | 5 |
| Korea (South) | 5 |
| China | 4 |
| Japan | 4 |
| Hong Kong (S.A.R.) | 4 |
| Israel | 4 |
| Taiwan | 3 |
| India | 3 |
| New Zealand | 3 |
| Austria | 2 |
| Malaysia | 2 |
| Germany | 2 |
| Canada | 2 |
| Saudi Arabia | 1 |
| Denmark | 1 |
| Italy | 1 |
| Viet Nam | 1 |
Where are Research Centres of Flexxon Patents Located?
List of Flexxon Patents
| Flexxon Patents | Title |
| US11934523B1 | System And Method For Securing Data Files |
| US11928210B2 | Module And Method For Monitoring Systems Of A Host Device For Security Exploitations |
| EP4022478B1 | Methods And Systems Using An Ai Co-Processor To Detect Anomalies Caused By Malware In Storage Devices |
| CN117216797B | System And Method For Protecting Data Files |
| DE602020031796T2 | Methods And Systems Using An Ai Coprocessor To Detecting Anomalies Caused By Malware In Storage Devices |
| AU2023201855B2 | Module And Method For Authenticating Data Transfer Between A Storage Device And A Host Device |
| NZ784312B | Methods And Systems Using An Ai Co-Processor To Detect Anomalies Caused By Malware In Storage Devices |
| SA522440461B1 | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Cybersecurity Threats |
| IL286431B | Module And Method For Detecting Malicious Activities In A Storage Device |
| KR102716978B1 | Methods And Systems For Detecting Anomalies Caused By Malware In Storage Devices Using Ai-Coprocessor |
| KR102695289B1 | Module And Method For Authenticating Data Transfer Between A Storage Device And A Host Device |
| KR102667827B1 | System And Method For Securing Data Files |
| EP4379583A1 | System And Method For Securing Data Files |
| IN202127031834A | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| AU2023266227A1 | System And Method For Securing Data Files |
| TW202424798A | System And Method For Securing Data Files |
| IN202334079825A | System And Method For Securing Data Files |
| IL304869A1 | System And Method For Securing Data Files |
| HK40101631A | System And Method For Securing Data Files |
| JP2024080605A | System And Method For Securing Data Files |
| US11610026B2 | Module And Method For Authenticating Data Transfer Between A Storage Device And A Host Device |
| EP3979118B1 | Module And Method For Detecting Malicious Activities In A Storage Device |
| AT1577188T | Modul Und Verfahren Zur Detektion Bösartiger Aktivitäten In Einer Speichervorrichtung |
| DE602020011800T2 | Module And Method For Detecting Malicious Activities In A Storage Device |
| MY199083A | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| SG10202202093XB | Module And Method For Monitoring Systems Of A Host Device For Security Exploitations |
| SG10202260284YB | System And Method For Securing Data Files |
| JP7368668B2 | A Method And System For Detecting Abnormal Behavior Of Storage Devices Infected With Malware Using An Ai Coprocessor |
| JP7202030B2 | Module And Method For Detecting Malicious Movements In The Storage Device |
| SG10202302682PA | Methods And Systems Using An Ai Co-Processor To Detect Anomalies Caused By Malware In Storage Devices |
| HK40077489A | Module And Method For Authenticating Data Transfer Between A Storage Device And A Host Device |
| HK40054686A1 | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| EP3899770B1 | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| CN114282228B | Module And Method For Detecting Malicious Activity In A Storage Device |
| CN113632083B | Systems And Methods For Detecting Data Anomalies By Analyzing Patterns Of Known And/Or Unknown Cybersecurity Threats |
| DK3899770T3 | System And Procedure For Detection Of Data Irregularities By Analysis Of The Morphologies Of Known And/Or Unknown Cyber Security Threats |
| IT202200066282T2 | System And Method For Detecting Anomalies Of Data Analyzing Morphologies Of Known And / Or Unknown Cybersecurity Threats |
| AT1523188T | System Und Verfahren Zur Erkennung Von Datenanomalien Durch Analyse Von Morphologien Bekannter Und/Oder Unbekannter Cyber-Sicherheitsbedrohungen |
| IL289367B | Systems And Methods For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| JP7092939B2 | Systems And Methods For Detecting Data Anomalies Through Morphological Analysis Of Known And/Or Unknown Cybersecurity Threats |
| KR102363182B1 | Module And Method For Detecting Malicious Activities In A Storage Device |
| EP4099618A1 | Module And Method For Authenticating Data Transfer Between A Storage Device And A Host Device |
| CN113939818A | Methods And Systems Using An Ai Co-Processor To Detect Anomalies Caused By Malware In Storage Devices |
| HK40060529A | Methods And Systems Using An Ai Co-Processor To Detect Anomalies Caused By Malware In Storage Devices |
| IN202124034054A | Module And Method For Detecting Malicious Activities In A Storage Device |
| CA3126591A1 | Module And Method For Detecting Malicious Activities In A Storage Device |
| MYPI2021004143A0 | Module And Method For Detecting Malicious Activities In A Storage Device |
| IL290159A | Methods And Systems Using An Ai Co-Processor To Detect Anomalies Caused By Malware In Storage Devices |
| AU2022200588A1 | Module And Method For Authenticating Data Transfer Between A Storage Device And A Host Device |
| AU2020337754A1 | Methods And Systems Using An Ai Co-Processor To Detect Anomalies Caused By Malware In Storage Devices |
| US11082441B1 | Systems And Methods For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| US11055443B1 | Module And Method For Detecting Malicious Activities In A Storage Device |
| SG10202105796SB | Module And Method For Authenticating Data Transfer Between A Storage Device And A Host Device |
| AU2020223632B2 | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| TWI740627B | Methods And Systems Using An Ai Co-Processor To Detect Anomalies Caused By Malware In Storage Devices |
| AU2021204804B1 | Module And Method For Detecting Malicious Activities In A Storage Device |
| NZ767245B | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| KR102323290B1 | Systems And Methods For Detecting Data Anomalies By Analyzing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| US20210064745A1 | Methods And Systems Using An Ai Co-Processor To Detect Anomolies Caused By Malware In Storage Devices |
| WO2021183043A1 | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| WO2021040618A1 | Methods And Systems Using An Ai Co-Processor To Detect Anomalies Caused By Malware In Storage Devices |
| VN82771A | Modules And Methods Of Control For Hazardous Activities In Storage Equipment |
| TW202134919A | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| NZ778067A | Module And Method For Detecting Malicious Activities In A Storage Device |
| SG10202004811XA | Methods And Systems Using An Ai Co-Processor To Detect Anomalies Caused By Malware In Storage Devices |
| CA3125101A1 | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
| SG10202009754QB | Module And Method For Detecting Malicious Activities In A Storage Device |
| SG10202002125QA | System And Method For Detecting Data Anomalies By Analysing Morphologies Of Known And/Or Unknown Cybersecurity Threats |
What are Flexxon key innovation segments?
What Technologies are Covered by Flexxon?

The chart below distributes patents filed by Flexxon in different countries on the basis of the technology protected in patents. It also represents the markets where Flexxon thinks it’s important to protect particular technology inventions.

R&D Focus: How has Flexxon search focus changed over the years?
EXCLUSIVE INSIGHTS COMING SOON!
Interested in knowing about the areas of innovation that are being protected by Flexxon?


