Imagine a cybersecurity landscape where every access request – whether from a trusted employee in the office or a remote partner across the globe – is met with rigorous verification. This is the foundation of Zero Trust Architecture (ZTA), a transformative approach that replaces the legacy “trust but verify” model with a more resilient principle: “never trust, always verify.” In an era where cyber threats are increasingly sophisticated and unpredictable, Zero Trust offers a proactive framework for securing data, systems, and networks.
Over the past two decades, ZTA has evolved from a conceptual framework into a cornerstone of enterprise security strategy. This evolution is reflected in the surge of patent filings, signalling robust innovation and growing investment in Zero Trust technologies. From identity and access management (IAM) to AI-powered threat detection, the patent landscape reveals how organizations are leveraging cutting-edge tools to fortify digital infrastructure.
What makes Zero Trust so compelling is its adaptability and integration with emerging technologies. For example, Artificial Intelligence (AI) and Machine Learning (ML) are increasingly embedded within Zero Trust frameworks, enabling real-time threat detection, behavioural analytics, and automated response mechanisms.
This report explores the trajectory of Zero Trust Architecture patents, offering a data-driven view of innovation trends, key players, and technological breakthroughs. Whether you’re an IP analyst, cybersecurity strategist, or innovation leader, these insights will illuminate the next frontier of digital defense.
| Category | Challenge | Description |
| Integration with Legacy Systems | Difficulty adapting old infrastructure | Most organizations still rely on legacy, perimeter-based systems that are not designed for Zero Trust. Integrating these with new authentication, identity, and network segmentation models requires major overhauls and costs. |
| Identity and Access Management (IAM) | Ensuring continuous authentication and authorization | Managing user and device identities across hybrid environments is complex. Implementing continuous verification without affecting performance or usability remains one of the hardest ZTA goals. |
| Scalability and Complexity | Managing Zero Trust at enterprise scale | Applying Zero Trust principles (verification, segmentation, least privilege) across large, multi-cloud, IoT, and remote ecosystems introduces technical complexity and high operational overhead. |
| Cost and Resource Investment | High implementation and maintenance costs | Deploying Zero Trust demands new technologies, extensive monitoring, skilled personnel, and cultural shifts—posing a challenge especially for mid-sized enterprises. |
| Balancing Security and User Experience | Over-verification vs productivity | Strict verification steps, frequent re-authentication, and policy enforcement can slow workflows and frustrate users, leading to resistance or poor adoption rates. |
Why Zero trust model needed?
Real-World Example: Google BeyondCorp
The Challenge:
Google faced a major cyber-attack in 2009 (Operation Aurora), which exposed vulnerabilities in traditional perimeter-based security. Employees working remotely or from different offices needed secure access without relying on VPNs or firewalls.
The Solution: Zero Trust Architecture
Google built BeyondCorp, a Zero Trust framework that assumes no device or user is inherently trusted, even inside the corporate network.
Here’s how it works:
Google’s BeyondCorp system continuously checks every device (laptop, phone, or tablet) for security updates, encryption, and patches before allowing access. Employees must verify their identity using multi-factor authentication, and their access is determined by their role, location, and device security status. Access to applications is granted only when both the user and device meet strict security criteria – for example, developers can only access code repositories from secure, company-issued laptops with current patches.
What is the patent filing trend in the Zero Trust Architecture?
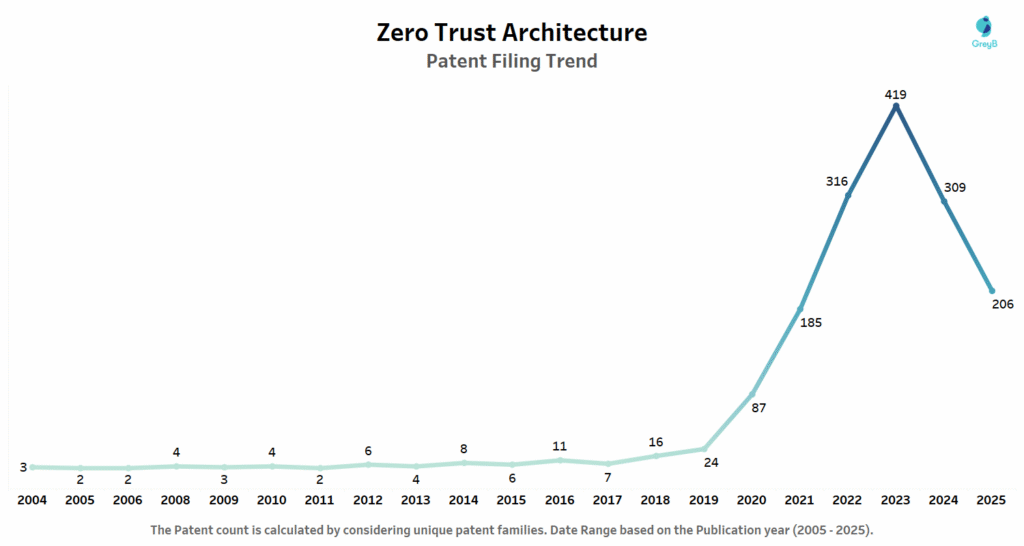
Are you wondering why there is a drop in patent filing for the last two years? It is because a patent application can take up to 18 months to get published. Certainly, it doesn’t suggest a decrease in the patent filing.
The answer is simple: companies got scared. After 2018, cyber-attacks became more frequent and more damaging. The old “build a wall and trust everyone inside” approach was clearly failing. Meanwhile, employees were working from home, using cloud apps, and accessing company data from coffee shops. Traditional security just couldn’t keep up. Zero Trust offered a better way – treat everyone as a potential risk and verify every single access request.
The Zero Trust market is growing rapidly, expected to increase from $34.50 billion in 2024 to $84.08 billion by 2030. As this expansion continues, companies are viewing their patents as valuable assets that will help shape the future of digital security and protection.
Technology Breakdown of Zero Trust Architecture
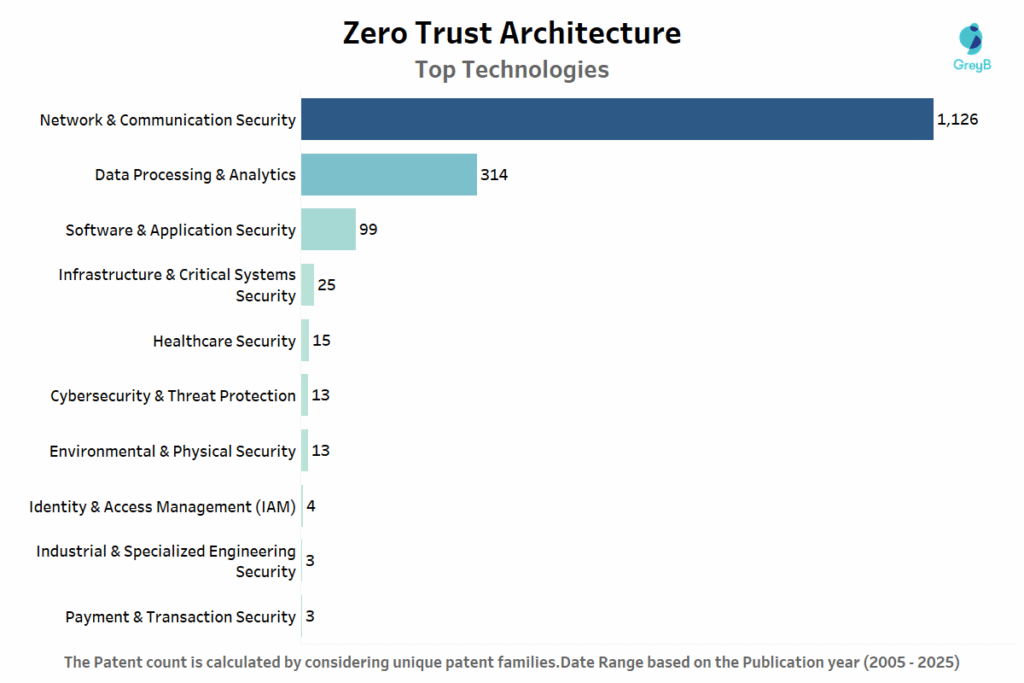
The patent landscape in Zero Trust Architecture shows a clear focus on securing how systems communicate. Network & Communication Security leads by a wide margin with 1,126 patents, showing that most innovation is happening around protecting data as it moves across devices, users, and networks.
Next in line is Data Processing & Analytics with 314 patents, highlighting the growing need to understand user behaviour and detect threats in real time. Software & Application Security follows with 99 patents, reflecting efforts to secure apps and platforms where users interact.
The majority of patent activity in Network & Communication Security is concentrated in Digital Communication, with 1,041 filings. This reflects the core role of secure data exchange in Zero Trust systems, where every message, transaction, and access request must be verified and encrypted. Innovations in this area often focus on secure protocols, identity-aware routing, and real-time data protection across cloud and hybrid networks.
Wireless Communication follows with 79 patents, showing growing interest in securing mobile and remote access environments. As Zero Trust expands beyond fixed networks, technologies like secure Wi-Fi, 5G access control, and encrypted mobile channels become essential. The remaining categories-Signal Transmission, Cable Installation, and Radio Navigation-have minimal activity, suggesting niche applications or foundational infrastructure that supports broader Zero Trust strategies.
| Network and Communication Security (Level 2) | Count |
| Digital Communication | 1041 |
| Wireless Communication | 79 |
| Signal Transmission | 4 |
| Cable Installation System | 1 |
| Radio Navigation | 1 |
Curious how your R&D or IP portfolio compares with these Zero Trust innovation trends? Request a Customized Zero Trust Innovation Report – get a tailored analysis of your patent landscape, mapped to emerging technology hotspots.
Key companies filing patents in Zero trust architecture
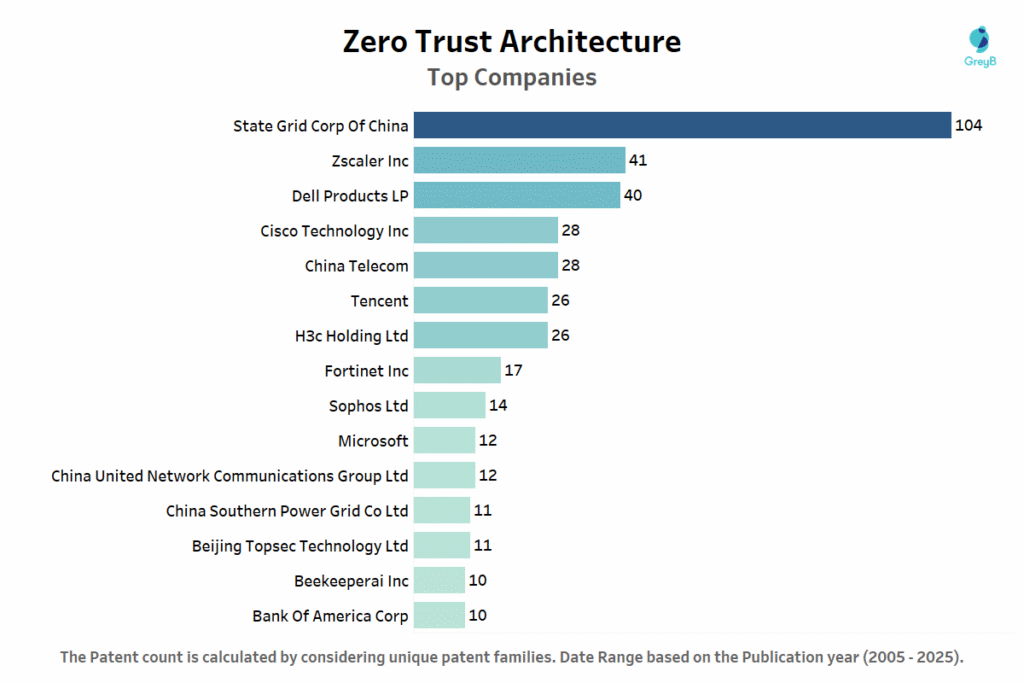
Did you know State Grid Corp of China leads the pack with 104 patents, more than double anyone else. Zscaler Inc. follows with 41 patents and Dell Products LP with 40. These numbers show who is investing the most in Zero Trust innovation.
The competition is truly global. American companies like Cisco (28 patents), Microsoft (12), and Hewlett Packard Enterprise (10) are competing head-to-head with Chinese firms including China Telecom (28), Tencent (26), and H3c Holding Ltd (26). This mix of tech giants, telecom companies, and research institutions proves that Zero Trust has become a priority across industries and borders.
Technology Overview of Key Companies in Zero trust architecture
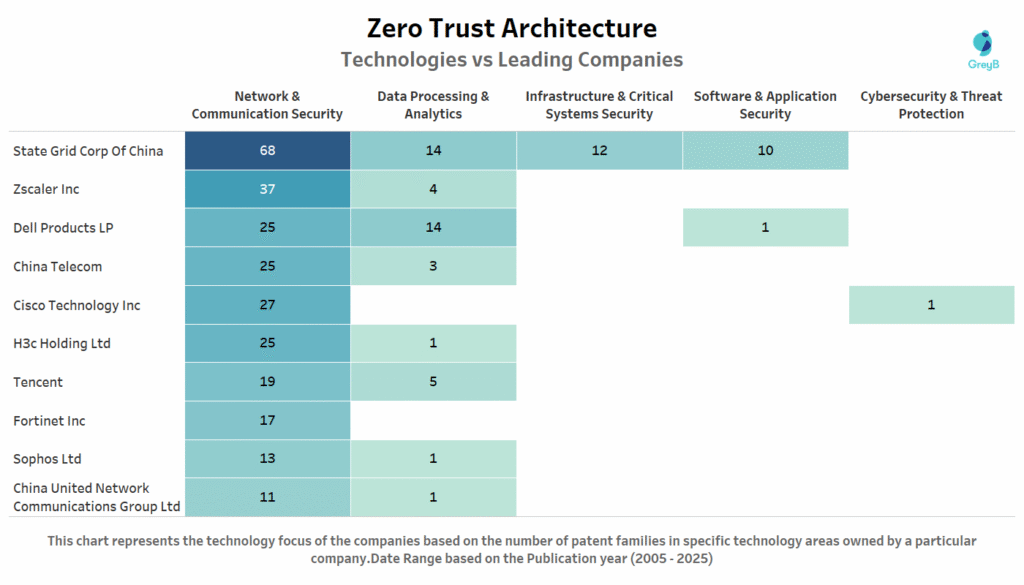
This chart exposes a critical blind spot in Zero Trust innovation: everyone is fighting over the same territory. State Grid Corp of China leads with 104 total patents but 65% (68 patents) focus solely on Network & Communication Security.
The pattern repeats across competitors-Zscaler, Cisco, China Telecom, and H3c Holding all concentrate 90%+ of their portfolios on network security. This clustering reveals defensive patent strategies rather than breakthrough innovation, with companies racing to protect incremental improvements in established technology rather than exploring new frontiers.
How many Patent did Zero trust architecture in different countries?
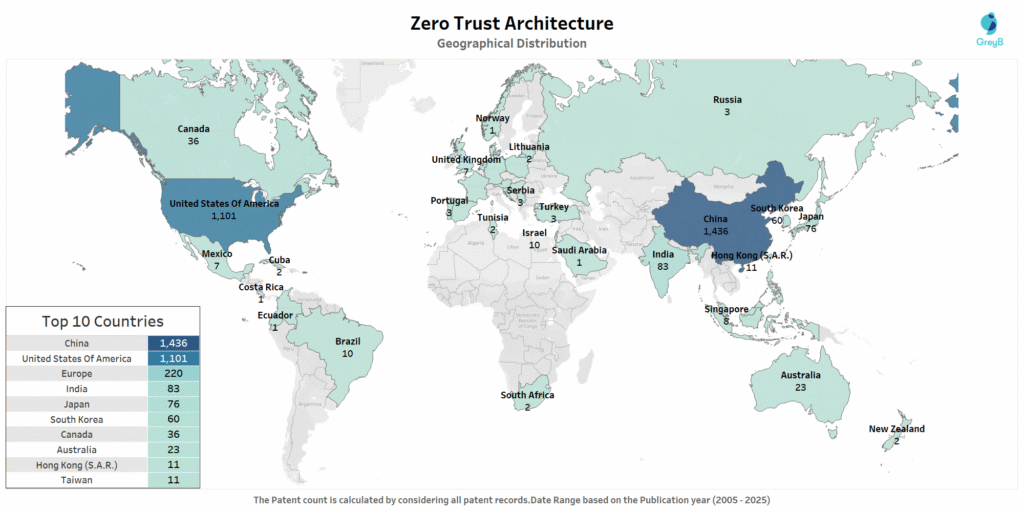
This chart shows where companies and organizations are filing Zero Trust patents worldwide from 2004 to 2025. China leads significantly with 1,436 patent filings, followed by the United States with 1,101 filings. Europe collectively shows 220 filings, while India (83), Japan (76), and South Korea (60) round out the top tier. This distribution reveals which countries view Zero Trust technology as strategically important and are actively protecting their innovations through patent systems.
Where are the Research Centres of Zero trust architecture patents located?
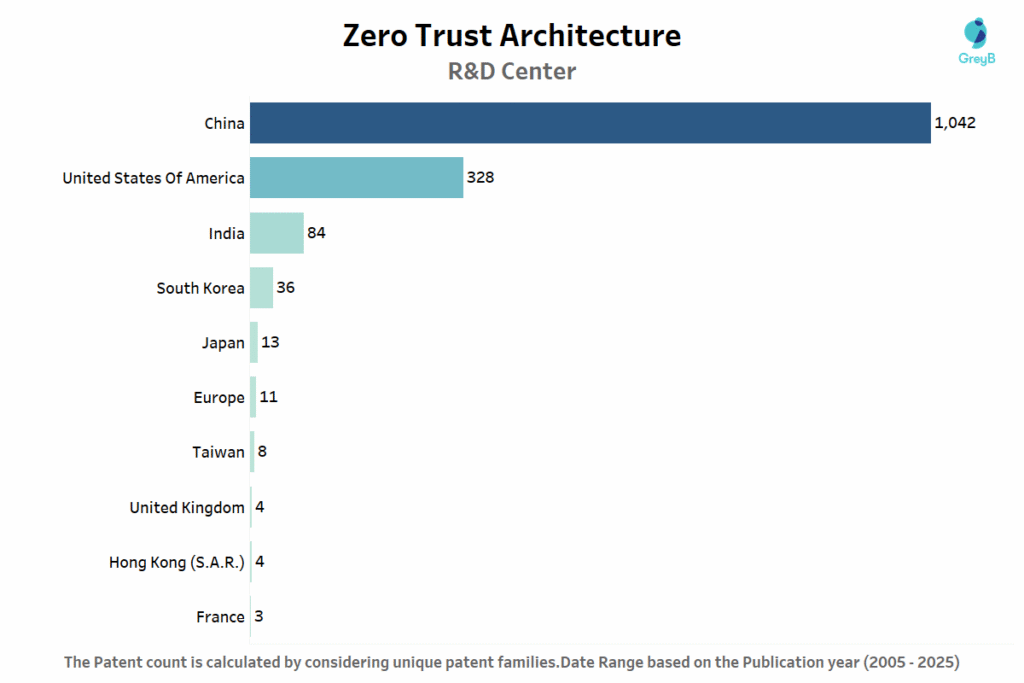
This chart identifies where Zero Trust technology research and development is most concentrated worldwide. China leads with 1,042 innovation centres, making it the global epicentre for Zero Trust R&D activity. The United States follows with 328 centres, while India emerges as the third major hub with 84 facilities. These numbers show where companies, universities, and governments are establishing labs and research teams to develop the next generation of Zero Trust security solutions.
What are the key inventors in Zero trust architecture?
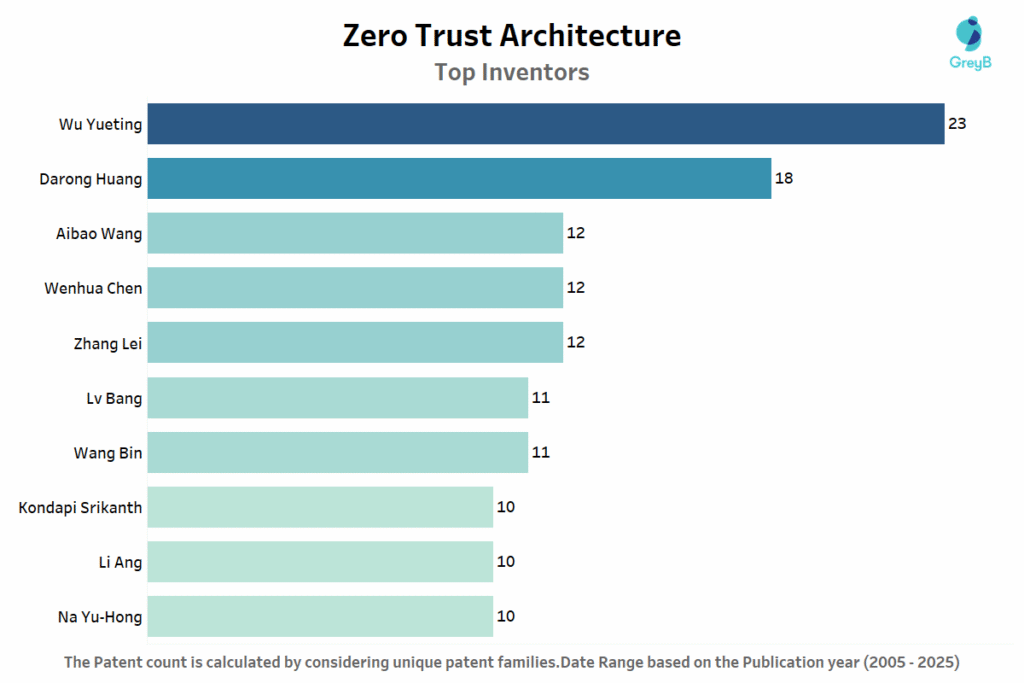
| Inventor | Associated Organisation | Count |
| Wu Yueting | Tencent | 23 |
| Darong Huang | Anhui University | 18 |
| Aibao Wang | China Telecom | 12 |
| Wenhua Chen | China Telecom | 12 |
| Zhang Lei | Nanhu Laboratory | 12 |
| Lv Bang | State Grid Corp Of China | 11 |
| Wang Bin | Hangzhou Hikvision Digital Technology Ltd | 11 |
| Kondapi Srikanth | Dell Products LP | 10 |
| Li Ang | State Grid Corp Of China | 10 |
| Na Yu-Hong | Anhui University | 10 |
This table shows the most active inventors in Zero Trust security, listing their names, affiliated organizations, and the number of patents they have contributed. Wu Yueting from Tencent leads with 23 patents, followed by Darong Huang from Anhui University with 18 patents, highlighting the key individuals driving innovation in this field.
How has the key companies patent filing trend evolved over the year in Zero Trust
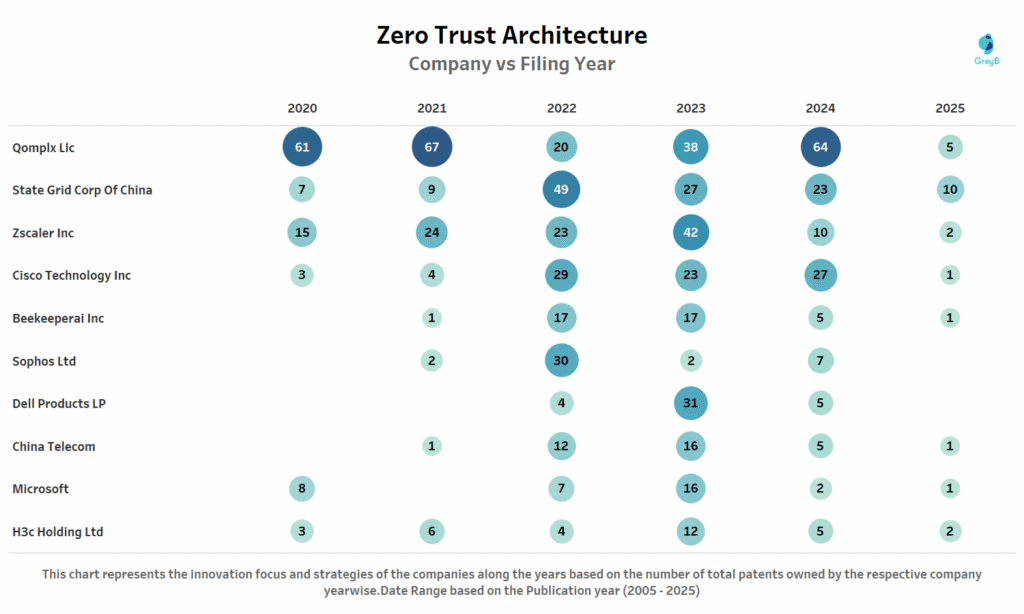
This bubble chart reveals dramatic shifts in Zero Trust patent strategies from 2020 to 2025. Qomplix LLC dominates with sustained high-volume filing-peaking at 67 patents in 2021 and maintaining 64 in 2024 before dropping to just 5 in 2025.
This pattern suggests either a completed patent portfolio strategy or a strategic pivot away from patent protection. State Grid Corp of China shows the opposite trajectory: surging from 7 patents (2020) to 49 (2022) before stabilizing around 23-27 annually, indicating a deliberate build-up phase followed by maintenance-level activity.
What is the Patent Legal Status of Zero trust architecture Patents?
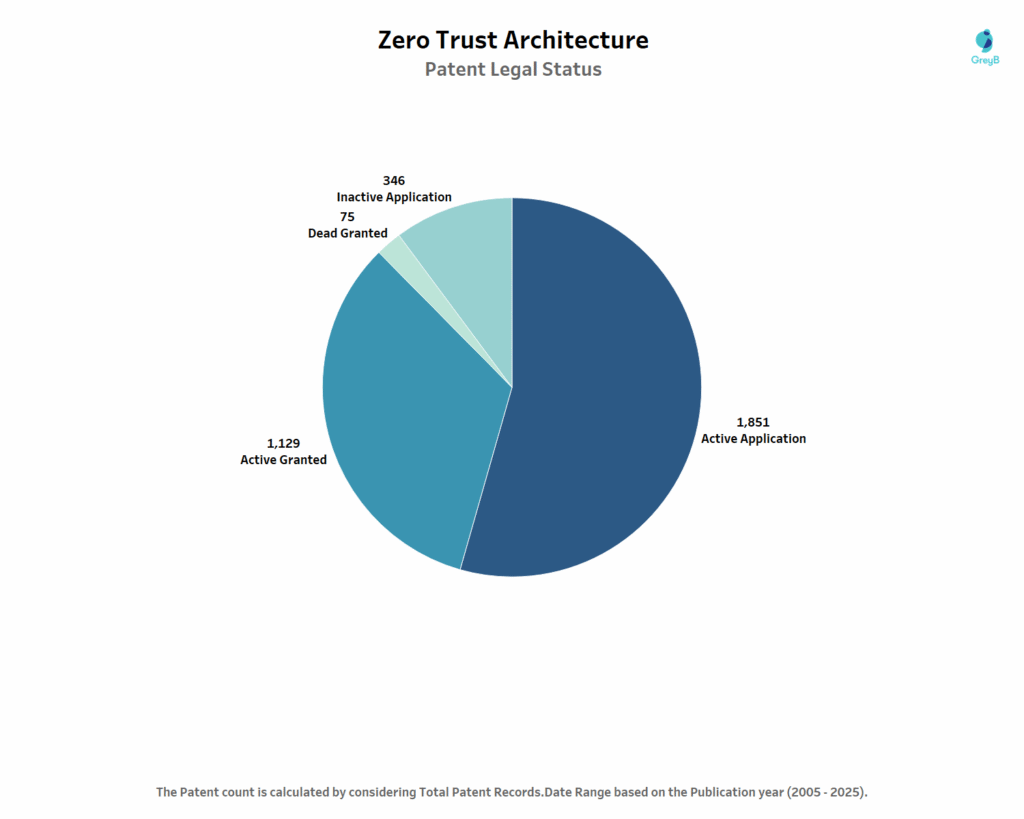
This chart reveals the health of Zero Trust’s intellectual property landscape. From 3,401 total patents, 2,980 (84%) remain active-either granted and enforced (1,129) or still pending approval (1,851). This high active rate signals intense ongoing innovation and strong commercial value, as companies continue investing in patent protection rather than letting applications lapse. The large number of pending applications suggests Zero Trust patent activity is accelerating, not slowing down.
Patent Grant Time Analysis in the Zero trust architecture
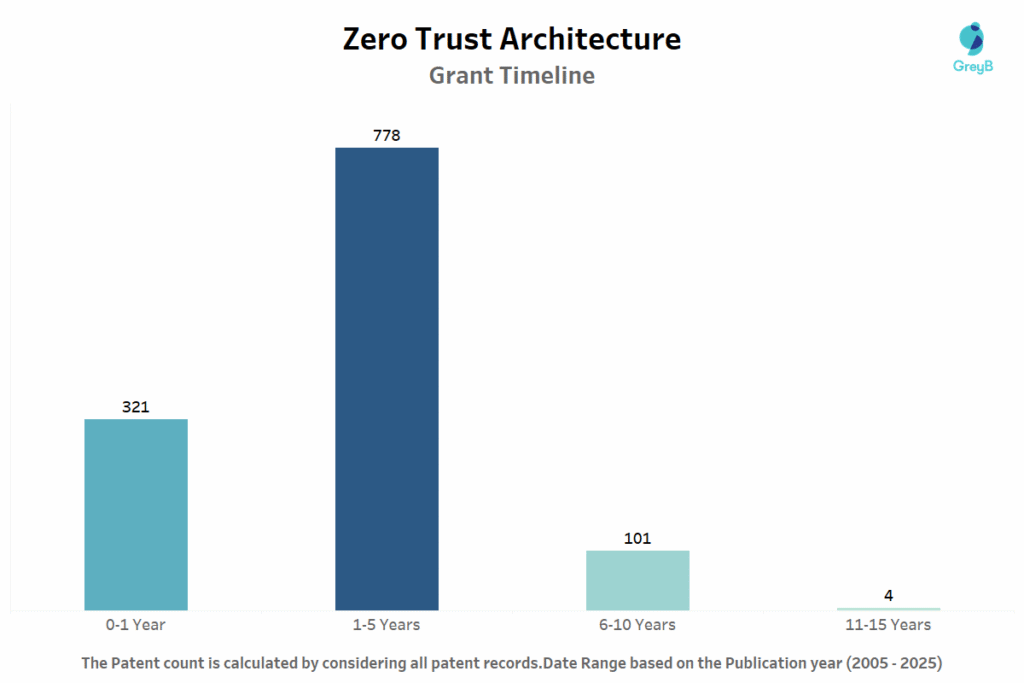
This chart shows how long it typically takes for patents in Zero Trust Architecture to be granted. Most patents – 778 in total-were granted within 1 to 5 years, which is the standard timeline for many cybersecurity innovations. A significant number, 321 patents, were granted in less than a year, suggesting fast-track approvals for technologies that may be urgent or well-prepared.
Top Cited Patents
This table presents the most frequently cited patents in Zero Trust security, showing the patent numbers, their assignee, and how many times each has been referenced by other patents. All top five patents belong to AT&T Intellectual Property I LP, with US9461706B1 being the most cited at 554 references, demonstrating the significant influence these innovations have had on the field.
| Patent | Assignee | Citation count |
| US9461706B1 | AT&T Intellectual Property I LP | 554 |
| US9544006B2 | AT&T Intellectual Property I LP | 485 |
| US9680670B2 | AT&T Intellectual Property I LP | 474 |
| US9742462B2 | AT&T Intellectual Property I LP | 471 |
| US9997819B2 | AT&T Intellectual Property I LP | 439 |
This section shows the most influential patents in Zero Trust security and explains how they solve everyday problems. The top-cited patents, all from AT&T Intellectual Property, address common challenges like slow internet connections, weak signals over long distances, and difficulty connecting remote areas.
These innovations help deliver faster, more reliable internet by using existing infrastructure smartly, whether through power lines or improved cable systems. Together, these patents demonstrate how leading security technologies are not just theoretical ideas but practical solutions that improve how we connect and communicate in our daily lives.
| Patent Number | Problem | Solutions | R&D/Industry Impact |
| US9461706B1 | Power lines only carry electricity and it’s expensive to add new communication cables everywhere, making it hard to connect remote areas. | Sends internet signals through power lines using special devices to keep signals organized, working with existing power infrastructure without new installations. | Brings internet to more places without installing new cables, helps create smart electrical grids, and saves money on building new infrastructure. |
| US9544006B2 | There’s limited space for sending data and we need to send more information without installing new cables or using multiple channels on one line. | Sends multiple data streams at the same time using different patterns to keep signals separate, with senders placed at different positions around the cable. | Delivers much faster data speeds and allows more people to use the same line while making better use of existing equipment. |
| US9680670B2 | Signals get messy when traveling long distances, causing data to mix together and quality to drop, which leads to slower and unreliable connections. | A smart system that fixes signal problems automatically using multiple sending points and adjusts based on current conditions to keep data clear and separated. | Provides faster and more reliable internet with better quality for streaming and downloads, helping signals travel farther without problems. |
| US9742462B2 | Old DSL internet lines are slow and need improvement, but it’s hard to upgrade without replacing everything which costs a lot of money. | A new way to send signals through existing cables that works with current DSL equipment and sends data in both directions without needing expensive fibre optic cables. | Makes old internet lines work better and saves money by using existing cables, improving home internet without major changes to the system. |
| US9997819B2 | Smartphones and devices need more internet speed, but phone towers can’t handle all the data traffic from voice, video, and internet services. | A new type of cable that sends signals without needing a return wire and can carry both power and data at the same time using very high frequency waves. | Helps build better 5G networks and makes it easier to add more cell towers, offering new ways to connect devices to the internet. |
Conclusion:
Most Zero Trust patents are approved within 1 to 5 years, which is the normal timeframe for security innovations. Interestingly, 321 patents were granted in less than a year, showing that some urgent or well-prepared technologies receive faster approval. This demonstrates that while the patent process is thorough, important cybersecurity innovations can move through the system more quickly when needed.
Wondering how these challenges reflect in your company’s innovation or patent strategy?
Request your Customized Zero Trust Innovation Report – get tailored insights mapping your IP portfolio to the latest global trends

